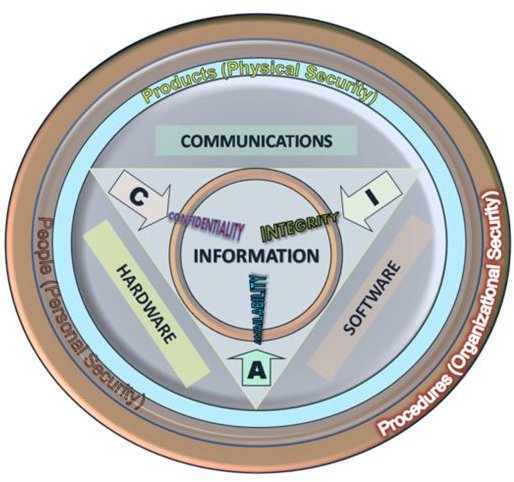
Fundamental Principles of Information Security
The Structure of Data
There are multiple ways to look at data information. One is the physical structure–where it is located, how it is stored. The other is the integrity structure of the data. Is it in the same condition as when it was saved or is it corrupt? Physical structure and integrity are two parts that must have policies to protect them. It’s important to understand that these two components, though separate, are equally important to creating a set of guidelines and principles of information security.
Information Protection, Back-Up and Recovery
So let’s start with the physical components of data. We know that it will be stored on a physical hard drive, a USB device or a CD. So information security involves protecting data to make sure that it can work in the way that it is supposed to. A file can run on software that it was designed for. It also includes making backups to store data off site, and having a well understood recovery policy. In this context, we are talking about the physical protection of the data.
See Also: Information Security Concepts: Confidentiality, Integrity, Availability, and Authenticity
Information Integrity
The next aspect of information involves its soundness. Has it been modified, or is it in the same condition as when it was stored on a hardware device? This means that the information has to be protected from malware, viruses or worms. It must also be protected from inadvertent operations on it, like modification. The information administrator should employ appropriate authentication and verification safeguard measures so that the information can be trusted to be accurate. This involves having secure passwords, the correct permission attributes to files and folders, and assigning the correct security permissions to individuals.
See Also: Information Security Concepts: Integrity
Access to Information, Information Confidentiality and Disclosure
In order to maintain the viability of information, certain policies must be in place. We’ve touched upon them in the information integrity section whereby we looked at passwords and permissions. The policy that must be in place here is more than one instituted by the IT department; it must be one where managers and executives fully understand how to use the data in their system as well as who uses it.
The value of information as an institutional asset comes from widespread and appropriate use; and its value diminishes through misuse, misinterpretation, or unnecessary restrictions to its access. Therefore the high-level authorization for the use of data will set the stage for how and by whom data can be used. This goes a long way in protecting the data’s integrity and also protecting the organization.
In such a case, information should be coded as fully accessible, moderately accessible or restrictive. This can set the stage to how the data will be accessed, who can access it, the permission levels available, the authentication schemes and its proprietary use.
See Also: Information Security Concepts: Confidentiality
Information Use
There should be a clear policy about what to use the information for. This can only be a part of the larger enterprise scheme on handling information assets. Think of it like this: A manufacturing plant may consider how assets are handled and who can handle them also how they are to be maintained. The same goes for information; it is an asset and must be treated as such.
Summary
We have covered several principles of Information security. These are information protection, back-up and recovery; information integrity, access to information, information confidentiality and disclosure; and information use. By looking at these principles in the context of information assets, then a reliable and pliable policy setting can be put in place for the enterprise.
See the article on the Top 5 Layers of Information Security
References
Source: WatsonBusinessSystemsLtd. The ISO 27001 Perspective: An Introduction to Information Security, Retrieved at https://security.practitioner.com/introduction/