Why Is Cross-Border Cybercrime Expanding Rapidly - International Cybercrime Growth
The Explosion of Cyber-stuff
Prefixing words with cyber has become all the rage in the media. Cybercrime, cybercriminals and cyberwar are all things we apparently
face. There’s a counter movement to quit looking at these attacks as something sophisticated and to think of them as they simply are: petty theft and crime. The fact of the matter is that stealing personal information from a remote location has become easier than ever and attackers often use automated tools to perform the job for them, rarely having any technical expertise or true understanding of how the tool operates. These tools are easily accessible and anyone with a slight technical inkling can operate them. To understand why these forms of attacks have been so rampant lately, we need to understand what has let us get to this point.
The Fashioning of the Internet
The Internet was not built to be a secure environment. The original architects of the network infrastructure looked more for stability and durability in their infrastructure than anything else. No doubt, none of the original architects of the Internet ever thought that millions of dollars would pass over global networks each day with users expecting to use the Internet as a safe haven for their credit card and financial information. As the Internet grew out of something that was purely academic into a commercial and then social space, innovative forms of security were built to lay on top of the original infrastructure. Unfortunately, much of the underlying design still relies on insecure methods of transport that can be easily hijacked or spied upon.
Hackers and Their Role in Information Security
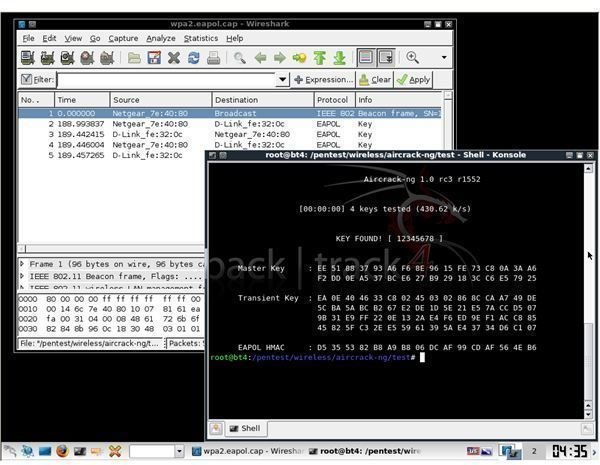
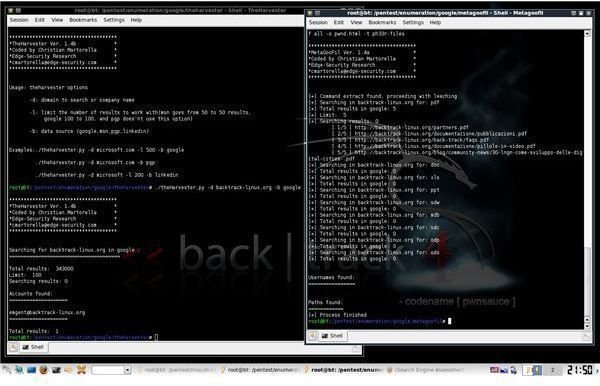
Today, many people get paid to be professional “hackers” or the more professional sounding “security researcher”. They enumerate vulnerabilities in information systems and develop tools to demonstrate those vulnerabilities. These tools are then released to the general public and are often used by the malicious to steal private information. The problem seems simple, right? If these hackers would stop releasing tools then we would stop having problems. Unfortunately, not all hackers work as security researchers and some produce tools to aid and execute criminal activities. These kinds of hackers are called black hats and are equally, if not more skilled, then their white hat counterparts. A lot of the information security field and the defense against cybercrime is a continuing race between these two parties.
Slow Adoption By Companies
Simply put, it’s not always profitable for companies to overhaul their entire system with security in mind. Unless the customer demands it, there is often no reason for a profit-minded company to redesign their systems. This can best be seen with the Facebook example, where secure sessions were not implemented until Mark Zuckerberg’s personal account was hijacked. There was no reason for Facebook to take user security into consideration until it became a personal problem. Many software companies are well aware of the vulnerabilities that attackers have found in their systems, but fail to repair the bad code because it would be unprofitable. This is why there are thousands of well documented, open holes in computer systems around the world. Additionally, hundreds of companies, including government entities, have horrible security practices that allow their websites to be scanned by search engine crawlers that then publish documents containing private information to public sources accidentally.
Enter the Rise of Cybercrime
These thousands of exploitable holes have been around long enough that applications have been developed that automate the
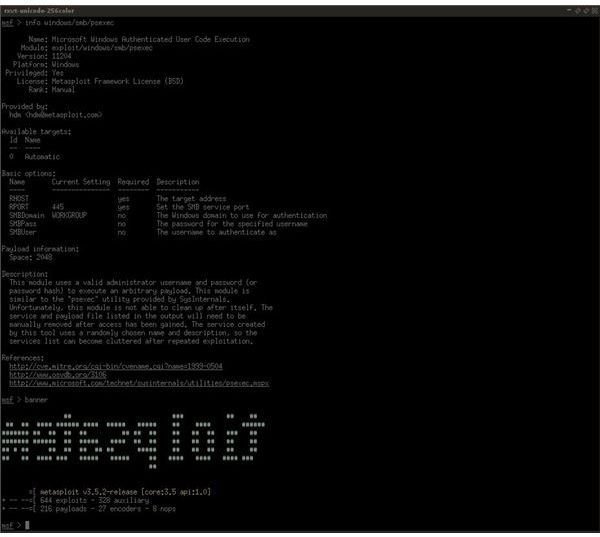
exploitation process. Non-technical cybercriminals can then utilize these applications, once they know where to find them, often by simply putting in a target’s location and clicking the go button. Even more tools exist that can continually crawl search engines looking for open company websites that allow access to sensitive PDF and XLS documents containing private information. Modern cybercriminals use a combination of these tools to exploit and gain information for identity theft and other criminal acts. With more and more tools coming out each year, cybercrime continues to grow at a rapid rate. Many security experts feel that the good guys are actually losing because of how easy and widespread these attacks have become.
Resources
Symantec: Security Predictions for 2011 - https://www.symantec.com/connect/blogs/internet-security-predictions-2011-shape-things-come
PC World: Top Security Predictions for 2011 - https://www.pcworld.com/businesscenter/article/212347/top_security_predictions_for_2011.html
Image Credit: Screenshots by the Author