Using Samurai To Prevent Attacks by Known and Unknown Vulnerabilities in Windows
Overview
Samurai is a simple security tool for Windows to protect against known or unknown vulnerabilities. It requires no signature to protect the computer but provide number of solutions.
Installation and System Requirements (3 out of 5)
Installation is not required in using Samurai. The program is a standalone executable. Upon executing Samurai.exe, the following files are created in the directory where you launched the program: samurai.cnt, samurai.hlp, urlhelp.dll and systrayhook.exe.
Systrayhook.exe is installed as a service in Windows and this will install whether you use or not any available security solutions by the program. Samurai will work for Windows NT, Windows 2000 and XP. It will work also in Windows Vista and Windows 7 by running it with administrator privileges but these OS are not officially supported.
Note that the samurai.exe is flagged with risk by some anti-malware scanner as
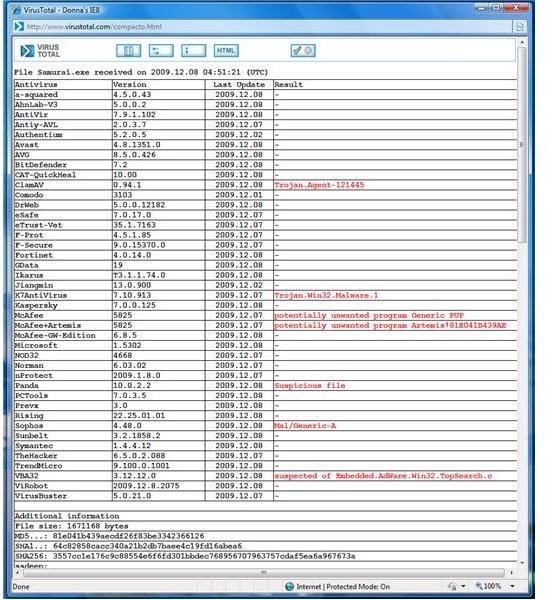
. I believe it’s false positive. The author of the program need to clear detection by the scanners. I scanned the system that has Samurai files and configuration in place during this review using Malwarebytes, SUPERAntiSpyware, A-squared, Spybot-S&D, The Cleaner, Windows Defender and Ad-Aware 2010 but all of these scanners found no risk or infection. Scanning using standalone rootkit scanners gave 0 infection.
Usage and Security Solutions in Samurai (4 out of 5)
To use Samurai’s solutions to known or unknown vulnerabilities that are currently or might affect Windows, you can select any or all of listed solutions:
- Disabling Windows Internet Naming Service, Web Authoring, uPnP service, spyware, shell URL protocol handler, RPC based DCOM, Remote Data Services Data factory, HTML Application MIME type, Guest Account, .grp file conversions, dynamic icons, dangerous URL protocols, automatic file open from explorer and known insecure activex controls.
- Preventing AIM URL protocol handler, anonymous sessions, DoS attacks, HTML frame and image exploits, LSASS exploits (Sasser based) and Internet Explorer pop-ups.
- Blocking of unsolicited inbound internet traffic and to delete backup password file (SAM file).
- Stopping the following services in Windows: Remote registry, Net DDE, Windows Messaging, Windows Indexing and Background Intelligent Transfer.
- Securing “My Computer” zone, HTTP configuration perimeters and license logging.
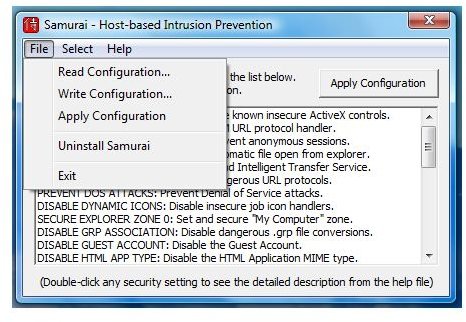
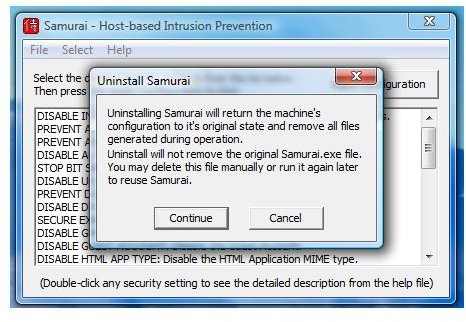
Any selected solutions will not take effect until you will click “Apply Configurations” button. There are also options to read or write the configurations that you previously applied. To remove Samurai’s security policies, you will de-select the solution and apply again. To permanently remove Samurai’s changes or modifications in the system, you will choose to Uninstall Samurai from its menu.
Images
Price to Value (5 out of 5)
Free to use but use with care!
Conclusion
Samurai has not been updated or maintained since 2007 and the download is not available in the author’s website but available in CNET.com, Beta News’ FileForum and Major geeks. Not recommended if you are using a not officially supported OS (Vista or Windows 7) by Samurai, fully patched Windows and have protection tools in place. IT administrators or experts or end-users with earlier unsupported OS will find this tool useful though.