Overview: Security Administrative Controls - Part 2
Detective Administrative Controls
Detective administrative controls are used to determine how well the security program is working. The most common controls in this category are:
- Security reviews and audits
- Mandatory vacations
- Background investigations of current employees
- Rotation of duties
Security reviews and audits
Reviews and audits are an important part of any security program. Not only should an organization develop a process to periodically check system, network, and procedure compliance. It should also consider an annual third party assessment.
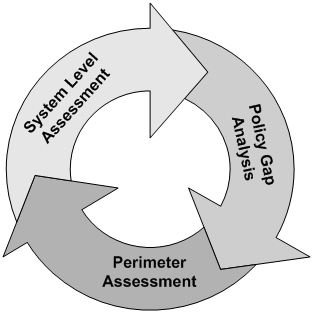
There are four areas of compliance included in an assessment: program policies and processes, system policies and processes, vulnerability tests, and penetration tests. It isn’t always possible to look at all four areas each year. Internal resource or cost constraints may make this difficult or impossible. In such cases, I recommend separating the four compliance areas into a rotating annual schedule. For example, a three year review and audit cycle might look like Figure 1.
The first year’s activities include a policy and procedure gap analysis. The assessing organization provides a final report listing areas where, in their opinion, improvements in policies and procedures can be made to improve the security program. It’s important to remember that risk management principles should be applied to any assessment recommendation.
During the second year’s assessment, the assessing organization tests for vulnerabilities in the network perimeter, including perimeter penetration tests and the use of tools and techniques that determine if well-known vulnerabilities exist in your perimeter device configurations.
The activities in the third year are similar to those in year two; the primary difference is scope. In year three the focus is on some or all of an organization’s business systems. The cycle begins again in year four.
An organization might also have to undergo regulatory audits by independent auditors. Regulatory compliance with legislation like the HIPAA and Sarbanes-Oxley should be an important part of your internal reviews and audits
Mandatory vacations
This is a control suggestion that’s often met with raised eyebrows. I know I initially questioned the effectiveness of making employees take time off. However, mandatory vacations can add significant value to detection efforts.
When an employee takes a week off, someone else typically has to take over her responsibilities. This new set of eyes can identify intentional and unintentional actions taken by the absent employee, which may negatively affect the confidentiality, integrity, or availability of your information assets. Mandatory vacations can also act as a deterrent to possible intentional malicious or self-serving activities. If a person knows he has to take a vacation, he might be less likely to perform illegal or unethical acts.
Another reason your employees should take time off is to reduce personal stress levels. An employee who is under considerable stress each day, and refuses to take time off, is more likely to make a mistake that compromises the integrity of your information.
Background investigations of existing employees
It might not be enough to conduct background checks during the hiring process. Employees who are promoted to positions in which they handle more sensitive data are candidates for an additional background check. It’s also a good idea to conduct periodic checks on employees who consistently handle highly sensitive or critical information. In both cases, investigations can reveal activities that constitute possible security policy violations or the potential for the commission of such violations.
Rotation of duties
The benefits of rotation of duties are almost the same as those realized from mandatory vacations. Employees are less likely to commit a voluntary illegal or unethical act when they know another set of eyes will regularly view the results of their work. A side benefit is the potential to cross-train employees to perform important business tasks.
The administrative controls we’ve reviewed are only as effective as the employees’ level of understanding of the policies, procedures, standards, and guidelines, combined with the willingness on the part of supervisors and managers to adhere to and enforce the security program. Both employee and manager compliance is dependant upon strong security awareness. Unless employees are aware of management’s security expectations, they can’t be expected to comply with them. And unless employees are convinced of the need for the extra effort required every day to secure your information assets, enforcement will require frequent use of sanctions, resulting in employee resentment and intentional non-compliance.