Security Policy Compliance and Testing Guide
Determining Your Data Security Policy
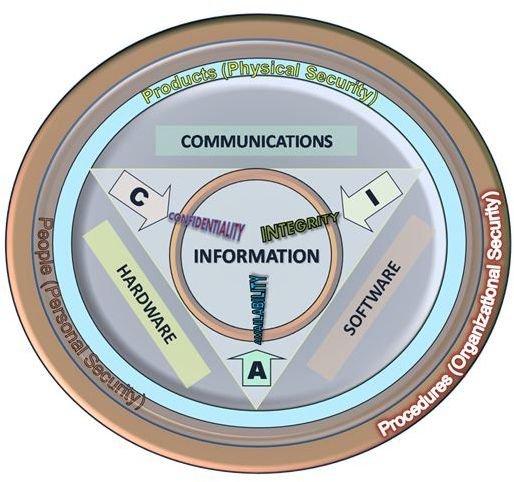
Having a security policy is vital for any business that employs one or more individuals. Such a policy will determine exactly how computers, data and any related hardware (mobile phones, printers) can be used. The idea is that a data security policy will outline any restrictions of use as well as specify requirements for passwords and usernames, restricted websites and other online services as well as confirming what security is required for the corporate network.
A data security policy should be looked upon as a statement of intent and a list of instructions. Some elements that are included in the policy may not yet be implemented, but they should be treated as if they are.
- Setting IT Security Policy
- Securing your Network with Policies and Procedures
- Security Basics - Components of Security Policies
- Storage Security Policies: What You Need to Know
- Understanding Internet Security - Policy & Confidentiality
Communicating Policy to Colleagues
Once a data security policy has been discussed, outlined and drawn up, it should then be published and communicated to employees and colleagues.
This is the most difficult aspect of developing this type of policy, as many employees will be largely apathetic to the requirements. As such, communicating the policy through security awareness training is vital so that employees can say that they know what the security policy is.
The policy should also include details of the incident management process, and this should also be communicated to employees along with the organization’s own responsibilities concerning workplace privacy and the law.
- What Is Your Employer’s Computer Security Policy?
- Communicating a Security Awareness Training Policy
- The Data Security Incident Management Process: Policies, Teams, and Communication
- Computer Workplace Privacy and Law
- The ISO 27001 AND 27002 Information Security Standards
- A Basic Information Security Standards Checklist
Email Security Policies
One area that should not be overlooked is in the use of email. This popular communications method can be used to send single words or entire reports. Either may be commercially sensitive, which is why it is a good idea to have a restriction on the type of data that can be sent by email.
A common approach is to implement email scanning software that detects spam, inappropriate messages and attachments, then holds them for review by a mail administrator. This will usually occur with both incoming and outgoing email messages.
- Email Security Policy and Procedure Manual
- Top Email Compliance Tips
- Achieving Compliance with ProofPoint E-mail Security Solutions
- 5 Practical Ways to Achieve Corporate Email Compliance
Sharing Data Securely
Whether you’re sending data via email, saving it to a USB Flash device or portable hard disk drive or even printing it out, the secure sharing of data should be a vital aspect of your data security policy.
Smartphones should be secured using dedicated software as well as the old fashioned method of signing the equipment in and out, while a full and clearly explained policy for the use and security of fax machines should be included and disseminated.
Similarly, Flash drives should be labeled with serial numbers so that they can be signed out, while the positives and dangers surrounding cloud computing should form a major element of your security policy.
- Advice for Businesses on Securing Smartphones
- The Lack of Security in a Fax Machine and How to Secure It
- USB Flash Drive Security
- A Discussion of Cloud Computing Security Issues
When Data Privacy is Vital
In certain situations, the data stored by your organization may only be viewed by certain people. For instance, you may be working in the healthcare industry, or as a contractor to a defense department. In these situations a standard data security policy will need to be enhanced for the duration of the contract.
Various additional material will need to be added to the policy concerning privacy and communicating personal data in a non-identifiable manner (for instance by removing names and addresses from patient-based reports).
- HIPAA Compliance Tips
- DoD Contractors to be 8570.1 Compliant
- Information Security Concepts: Authenticity
- Information Security Concepts: Confidentiality, Integrity, Availability, and Authenticity
- Designing a High School Information Security Policy
Security Testing
Before you’re ready to draw up and implement the security policy, however, you will need to be aware of some of the testing tools and requirements that can be used for ensuring your network and systems are up to scratch.
There are various tools available for auditing your network security, but the best examples are those that test your network’s resilience to penetration testing and brute force intrusion.
Unfortunately, the mistake of many organizations is to assume that the threat will come from outside. In fact, many data breaches occur due to lost or stolen hardware or even physical intrusion into offices or server rooms.
- Do-It-Yourself Security Testing and Auditing
- A Beginners Guide to Penetration Testing
- The Top 5 Free Penetration Testing Tools
- Top Ten Free Security Tests
- PSExec: Free Security Testing and System Management Tool
- Fuzzing - the Brute Force Approach to Security Testing
References
- Image credit: Wikimedia Commons/JohnManuel