Simple Steps To Erasing A Hard Drive
Why Reformatting Isn’t Enough
While a high-level format will make the hard drive appear empty by removing the partition table and boot sector, the formatting process doesn’t destroy any actual data. With a few minor exceptions, such as formatting with a different file system than the original, (i.e. NTFS instead of FAT32 over a former Windows XP installation) the magnetic regions on the hard drive sectors are left largely intact until new data is written to replace the old.
Nuke It!
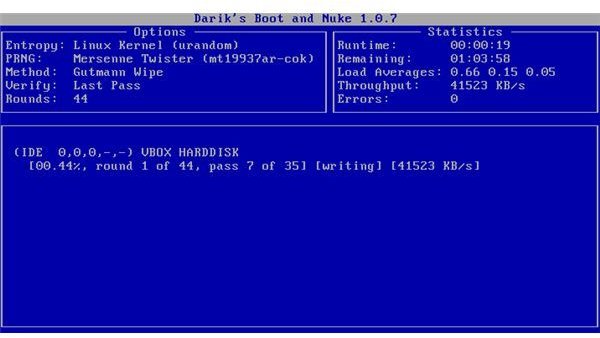
If you want to prevent the possibility of data recovery, you’ll want to zero out your hard drive, or better yet, overwrite each sector with random numbers. An excellent utility for this is Darik’s Boot and Nuke (DBAN.) It’s a powerful, free application that uses the United States’ Department of Defense (DoD) cleaning and sanitizing standard for erasing hard drives. The steps involved in using DBAN are simple:
- Extract the program to bootable media, such as a floppy disc, CD-ROM, or USB Drive
- Boot your system to the drive where you’ve installed DBAN.
- Type ‘autonuke’ at the prompt or press your ’enter’ key to manually select the overwriting algorithm to use, and the number of rounds and passes
- Allow DBAN sufficient time to complete the task. A higher number of passes and rounds will increase security, but will take more time.
FBI Forensics and Recovery
There remains a great controversy over the extent to which intelligence and law enforcement agencies can recover overwritten data. An often referenced paper, written by Peter Gutmann of the University of Auckland, “Secure Deletion of Data from Magnetic and Solid-State Memory,” explains possible methods of recovering overwritten data. A principle concept involved is based on the lack of precision in the write heads of most commercial hard drives. To simplify, the overwrite data may not entirely cover original data due to minor inconsistencies in rewriting. Some pieces of original data can be detected with sensitive instruments capable of distinguishing between “layers” of written data.
An article by the National Bureau of Economic Research, “Can Intelligence Agencies Read Overwritten Data?” is a direct response to Gutmann’s paper. It criticizes the paper for a lack of specific references and unsubstantiated claims. To determine the credibility of either article is not the point here, however. The simple fact is that, when concern over data reaches this level, physical destruction of the hard drive is the only 100% certain way to prevent recovery.
Degaussing and Physical Destruction
If your hard drive is damaged or intended never to be used again, the most reliable means of erasing data are degaussing, which demagnetizes the drive and renders it magnetically neutral, and physical destruction. Once a hard drive is degaussed, not only is the data removed, but the functionality of the drive is terminated as well. Methods of destruction include incineration, shredding, and corrosion.
Ultimately, among all the necessary steps to erasing a hard drive, the most important is to determine the consequences and likelihood of the data being recovered. If there is no reasonable risk of the HD ever being subject to forensic analysis, the DBAN wiping utility should provide adequate security.
Screenshot of Darik’s Boot and Nuke provided courtesy of www.dban.org