How does Phishing happen to you? Know Your Enemy (Email and Spam)
In the early days of Phishing, it all started out as harmless emails when a few pranksters just wanted a few passwords for fun. It is no longer fun and costs businesses millions of dollars – either to fight it or to pay for it. Although we do incorporate a lot of systems into place, there is a strong voice in the security Industry that the good vs. evil war will be on for quite some time and there are bound to be victims.
Some war! What if you were the Victim? You wouldn’t be satisfied with the incomplete status of this so called “war”, would you? However, if you know how phishing is done, you can be on high alert when you sense it, can’t you?
Email and Spam are the staple diet for the phishers and attackers, and they have been using it for years now since it is ubiquitous, almost free and the malicious mails can be distributed to live email accounts within hours ( and sometimes even in minutes if there is an establish network of Trojans). By leveraging the fake “Mail from: functions” by exploiting some loopholes in the SMTP (a common mail server communication Protocol), they impersonate any organization’s authority and make you believe these mails come from those organizations, luring you into giving your data away. They set the RCPT: function with an email id they can pick up mail from, thereby starting a process that can guarantee a deluge of emails from unsuspecting users full of data. Although many users are very aware of all of this, there are still some who fall prey.
Are there anything specific things in particular about emails that have been sent with the sole purpose of phishing? Here are a few check points:
- Do the emails look and sound a trifle too official?
- Are the emails badly worded, poorly written and littered with mistakes of all sorts? ( this is not as prevalent, because the dudes sending you the phishing mails have been seriously taking writing classes)
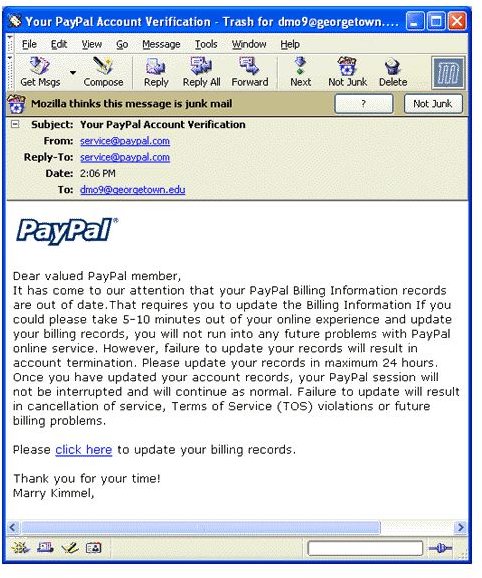
- Do you notice any minor URL changes? Like PayPal.com looking like pay-pal.com?
- Does your HTML on email look like it obfuscates URL target information?
- Do you see any standard attachments (the list is growing endlessly, by the way)?
- Do you see any fake “Mail from:” and rcpt : fillings?
- Do they ask you to enter secure data into a form they provide, or in a page they link to?
This check list may not save you; what really saves you is lapping up more of this information; being anal-retentive about the emails you receive; not being gullible and finally; not reading mail at all (not possible, eh?).
Learning from an Example :
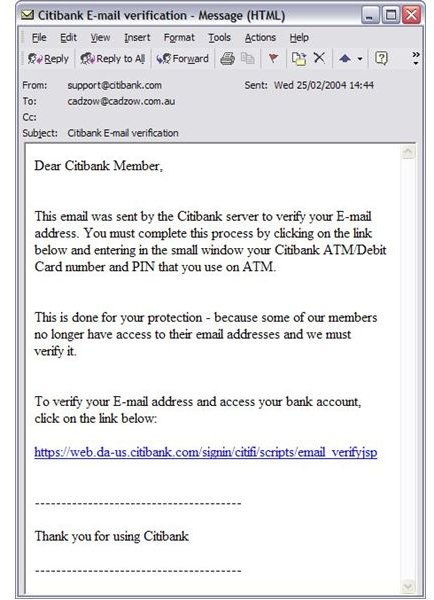
It would be great if we can take our lessons from a real life example of a Phishing email that has been sent from Citibank:
Images
So how do you know if this email is a phishing attempt?
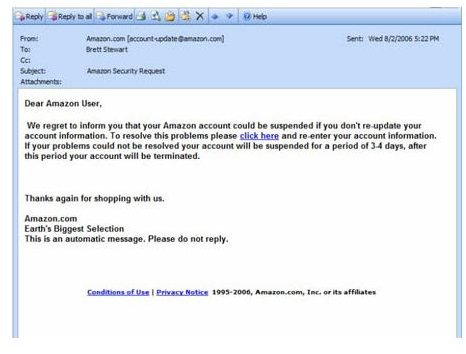
- Financial institutions cry till their throats go dry about the little fact that they never ever send out an email asking you to click on some link or the other.
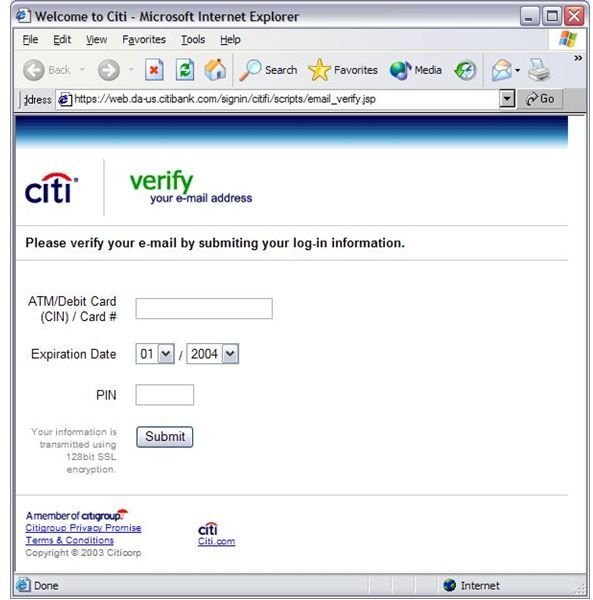
- The link provided herein takes you to the page shown below
Images
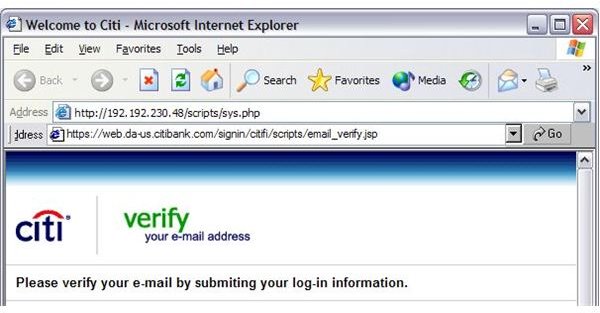
3. Note that once you land on the site that was supposed to have been that of Citibank’s – you suddenly don’t see a “padlock” icon even though the URL starts with " Https://" – that takes money and our little phishing group isn’t going to spend just as yet.
4. Finally, the address bar itself is a fake. If you go to view>toolbars> address Bar, it will immediately show you another address bar altogether. As shown below.
Images
Images
Related articles
>»> A Furtitive Peek into the History of Fishing
>»>Ignore Phishing and you are a Dead FISH
>»>Phishing Delivery Mechanisms: Know Your Enemy (Web based Attacks) - Part II