How to Use a Win32 Olmarik Trojan Remover
Trojan Olmarik is known to install a backdoor Trojan and rootkit in Windows and Mac operating systems. It is also known as Alureon, DNSChanger, TDSS and Backdoor Triplex. There are several variants of Olmarik which is why antivirus vendors continue to update the definitions to detect the malware.
Most antivirus vendors provide a Win32 Olmarik Trojan remover but not all scanners are successful in removing the Olmarik infection. Find out below what the Olmarik Trojan does and which scanner should be use to permanently remove an Olmarik infection.
Symptoms of Olmarik Trojan Infection
Many computer users don’t know if there is an Olmarik infection in their computer, until they attempt to install the Microsoft Security Bulletin MS10-015. This security bulletin update fails to install because the computer is infected with an Olmarik Trojan or Alureon rootkit.
When a computer is infected with an Olmarik Trojan, there are hidden files added in both the C:\Windows\System32 and C:\Windows\System32\drivers folders. They are not visible, even if you have configured Windows or Mac OS to show hidden files. This Trojan only becomes visible when a malware scanner with the capability to find rootkits is able to rename or remove the rootkit infection.
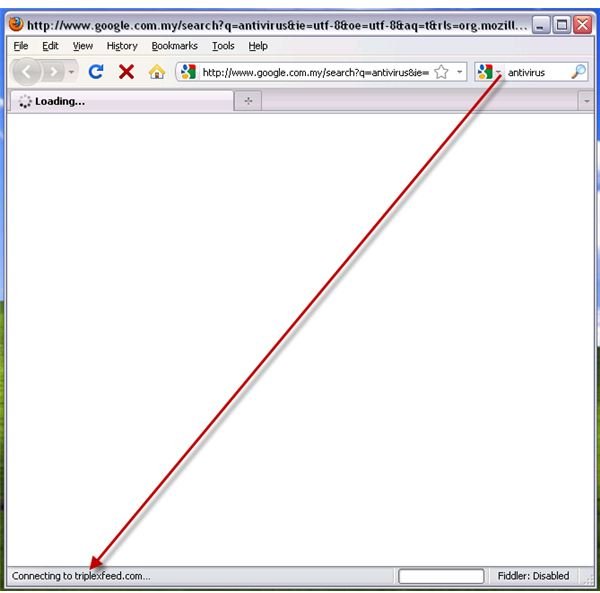
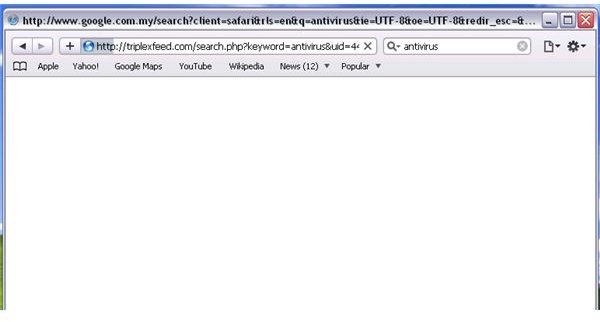
A successful installation by malware to infect the system with Olmarik Trojan will prevent any browser to visit web-searches. People can still use the search engines for keywords searches, and the result appears to be normal because the online search provider will display the search results. However, clicking on any search result items will not connect or load the websites that you choose to visit. Instead, the browser will connect to triplexfeed.com or tripledfund.com. The said domains are controlled or managed by Olmarik Trojan attackers. The computer information is sent to the domains so it can determine what else it can do to the infected machine, e.g., install a rogue antivirus program, serve illegitimate advertising, or download other types of malware.
Some variants of the Olmarik Trojan will modify the DNS server settings. Alternative browsers cannot escape from Olmarik Trojans because many browsers are affected such as Safari, Internet Explorer, Firefox, or Opera browser.
Removing of Win32 Olmarik Trojan
The free malware scanners that provide effective and automatic removal of the Win32 Olmarik Trojan are as follows:
-
TDSSKiller by Kaspersky. This tool is quite effective as reported by many Bright Hub members in the article, “Google Redirect Virus.”
-
Windows Malicious Software Removal Tool by Microsoft. This is already installed in Windows XP, Vista and Windows 7. Simply type mrt.exe in the Start > Run box and hit OK key to start scanning the system.
-
Hitman Pro - Note that Hitman Pro is free to use. You can use the trial version if you want it to remove any malware it detects.
-
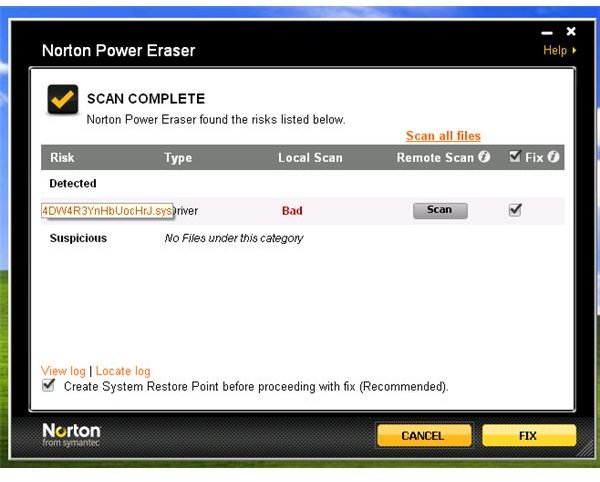
Norton Power Eraser by Symantec
-
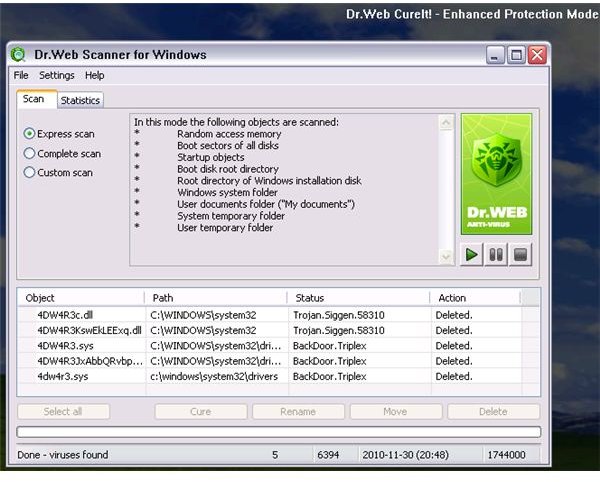
CureIt by Dr. Web
-
DNSChanger Removal Tool for Mac users
-
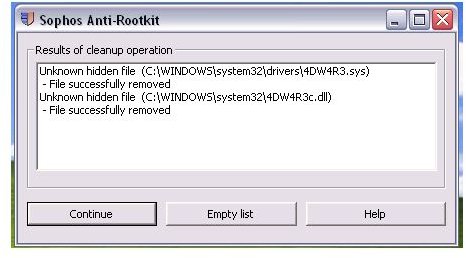
Sophos Anti-rootkit - Note that email registration is required to download from Sophos. Please be careful in allowing Sophos to remove all detected items.
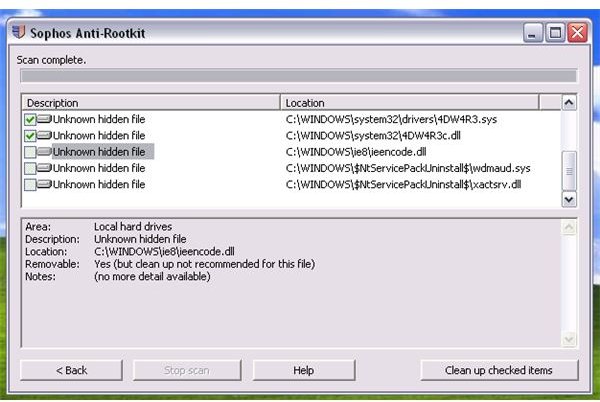
in legitimate and non-infected files occurred when I tested this in trying to remove the Win32 Olmarik Trojan.
You use the above tools to remove Olmarik Trojans and the rootkit. Most of the above tools will remove the rootkit infection in the first scan and removal process, but it will also leave some traces that are no longer hidden. To permanently remove the remnants, you need to run another scan. Note that remnants of malware do not pose security threats anymore since the rootkit and Trojan have been taken care of and removed.
Screenshots of Removal Tools for Win32 Olmarik
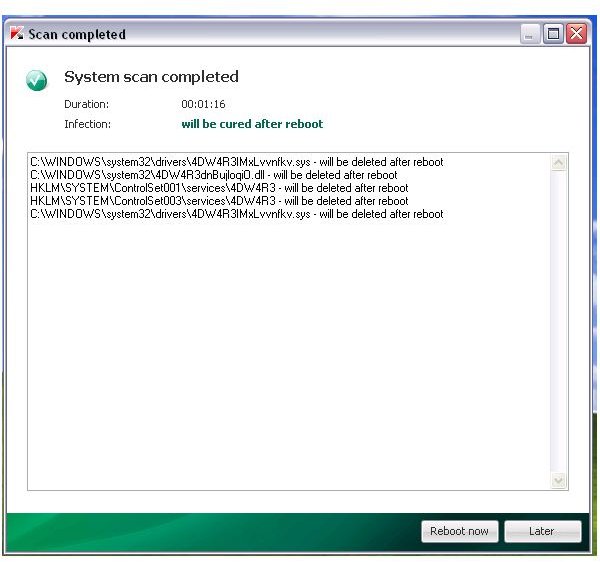
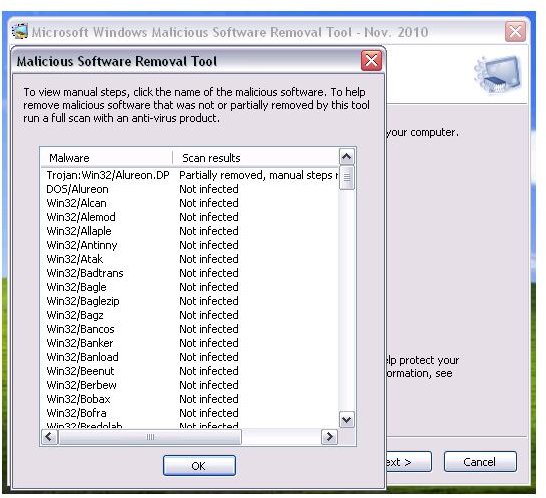
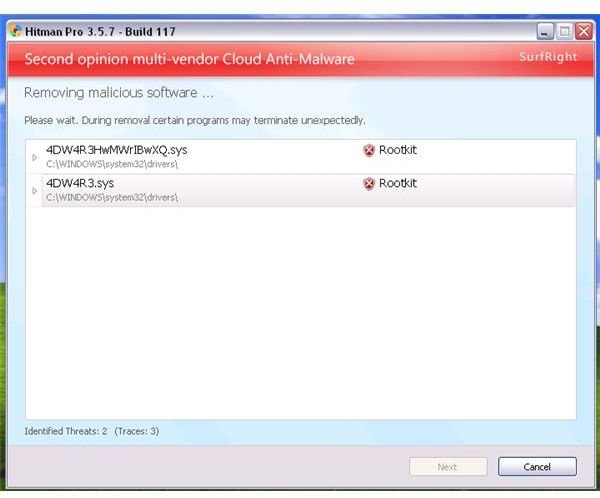
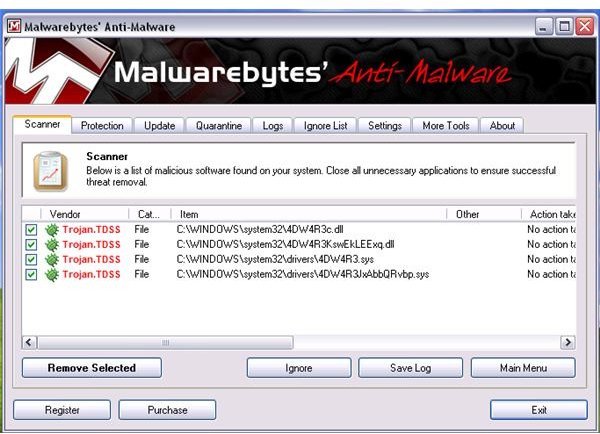
Removing Remnants of Win32 Olmarik Trojan
If you are an advanced-user, follow the next steps to manually remove the remnants of an Olmarik Trojan:
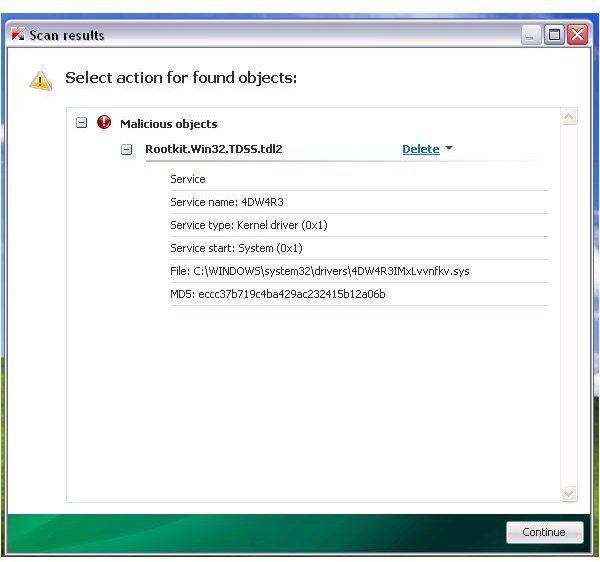
Note: Before you begin, you should have noted the driver, file or service names of the Trojan/rootkit infections that were removed by any of the above scanners. An example is the above image, where TDSSKiller and other tools has detected and removed the driver, service name and file of 4DW4R3IMxLvvnfkv.sys and 4DW4R3dnBujloqiO.dll. The files that you need to manually delete always start with the first 6 characters that the Trojan/rootkit is using e.g. 4DW4R3dnBujloqiO.dll.
- Browse to C:\Windows\System32 and C:\Windows\System32\drivers folder. Find and delete the files that the Trojan/rootkit has added e.g. 4DW4R3dnBujloqiO.dll, 4DW4R3dnBujloqiO.sys, 4DW4R3.sys and/or 4DW4R3.dll.
- Navigate to the following registry keys in Windows and then delete 4DW4R3 registry keys and the sub-keys:
- HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\4DW4R3
- HKEY_LOCAL_MACHINE\SOFTWARE\4DW4R3
Screenshots taken by the author.