Research on Network Security: Areas of Study
Why Study Network Security?
One of the nice things about network security is that it’s extremely applicable to the real world; after all, who doesn’t depend on the Internet in this day and age? Doing research on network security thus has immediate benefits for society.
Of course, the Internet is hardly the only place where network security research applies, but it’s definitely the largest and most important. Let’s take a look at some of the areas where active research is ongoing.
Internet Routing Tables and BGP Hijacking
Let’s start with a brief overview of how Internet routing works. In order to deliver a website or other file over the Internet, a computer must access it using its IP address. Of course, it would be impossible for the average router to store the IP addresses of every computer on the net, so if you’re surfing the web and type in a url, your computer first checks with a domain name server to find the IP address.
This lets the computer know what IP address we need to contact. How do we get to that address? When you request a webpage, your Internet Service Provider (ISP) looks at its routing table to determine what direction it should send the request off in. How does it build this table? The other computers that it connects to will advertise what they know about best routes to various areas of the Internet. Your ISP chooses the best one and stores that. For example, if server A can reach destination D in 5 time units and it takes 1 time unit to send traffic to D, while server B can reach D in 4 time units but it takes 3 time units to send traffic to B, then the table will show that traffic to D should be sent though A and will take 6 time units. (This is, of course, a simplification).
What if A doesn’t really have a short path to D, but is lying about it in order to steal traffic? What if A didn’t really send that message, but server E is impersonating A to steal traffic? What if server C falsely claims that it owns destination D, so all traffic going to D should be sent to it? These are some of the issues dealt with in BGP hijacking research.
Botnets and Other Dirty Tricks
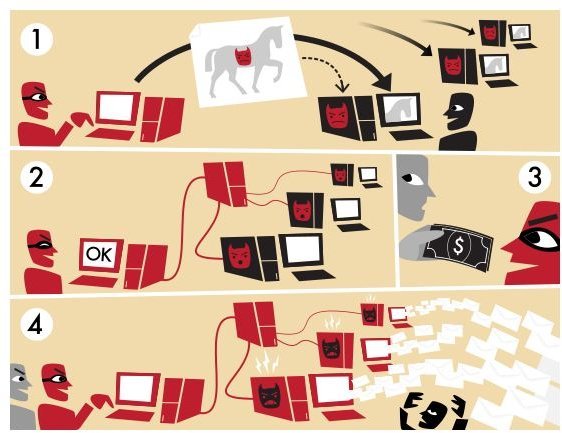
In the past, people wrote viruses for a very simple reason: to show that they could. Now, they do it for an even simpler reason: to make money. After gaining control of your computer, the bad guys can make money off of you in several ways. They can steal your credit card and bank account information and either use it or sell it. More commonly, they’ll add your computer to a botnet, a collection of
thousands or even millions of computers that can be rented out to anyone who wants to send out spam. It’s a great deal for the owner of the virus and for the spammers. They can send out millions of spam emails for only a few hundred dollars, and since it’s coming from a huge number of computers owned by people who for the most part have no idea what’s happening, they don’t have to worry about having their own computers or internet connection shut down. Of course, the rest of us pay for that with tons of junk email (along with slower computers, if we’re part of the botnet).
Obviously, this leads to several areas of research. How do we detect botnets? How do we defend against viruses? How do we recognize spam? These are all areas that could legitimately fall under the broad heading of (research on) network security.
Phishing
Many network attacks actually involve social engineering rather than any particular technological prowess. Social attacks involve talking people into giving you what you want, rather than taking it by force. One of the most famous hackers of all time, Kevin Mitnick, claimed that he broke into computers solely by using the passwords and codes he gathered by using social engineering, rather than using software.
One of the best known examples of scammers trying to talk you into giving up your private information is the 419 scam, named after the relevant section of the Nigerian penal code. The scammer informs you that he needs help transferring money out of the country, and offers you a percentage if he can use your bank account to hold the money. Amazingly, this scam has been working since before email became popular (when they would actually run it by post!). It actually dates to at least the 1920s!
Phishing, on the other hand, is closer to the traditional social engineering used by hackers like Mitnick. It involves convincing the user

that he’s talking to a trusted party, and then using this disguise to trick the user into turning over his information. Common examples are emails claiming to be from banks or from major websites, such as Ebay and Amazon. Generally the gist of the emails is that there’s a problem with your account and you need to log in immediately. On clicking the cloaked link, you find yourself on a fake site where, if you’re foolish enough to enter your account information, the scammers will have themselves another victim.
The question, then, is how do we automatically detect phishing sites? While some are fairly obvious (major banks are NOT going to send you emails full of spelling errors), others look quite genuine. While the simple solution is to always type such links directly into the address bar rather than clicking them, finding a technological solution is always easier than changing human nature.
Resources
Most major universities will be doing research on network security. At the author’s institution, Colorado State University, the network security group works on DNS security, particularly with regards to BGP hijacking, and has developed BGP monitoring software to help detect attacks in real time.
Sandia National Labs, which does research for the Department of Defense, has lately been focusing largely on cybersecurity. One of their tasks is capturing and disassembling viruses to find out how they work so that we can better defend against them.
Image Credits - Wikipedia Commons - https://commons.wikimedia.org/wiki/File:Botnet.svg & https://commons.wikimedia.org/wiki/File:Phishing.JPG