Using Cipher to Encrypt Your Database and Data on your Hard Drive
What is the Cipher Command?
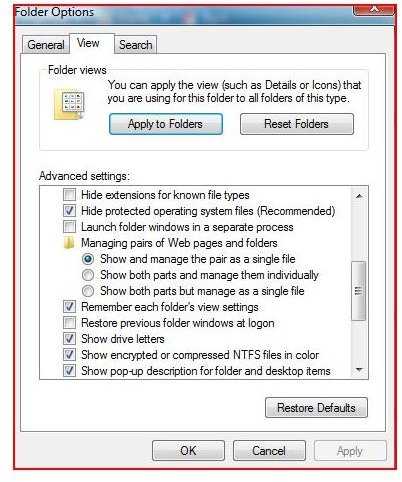
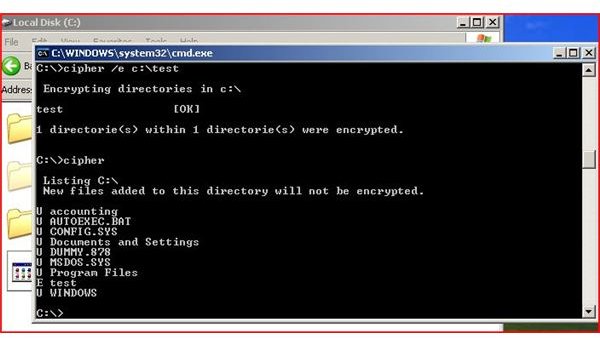
Windows XP and Windows Vista contain a command to encrypt files or to check files to see which are encrypted. Using the command prompt, you can navigate to the file or folder and run the command. A ‘U’ in front of the name means the folder or file is unencrypted and an ‘E’ indicates the folder or file is encrypted. This command is generally used by the IT professional community when working with files from the command prompt. Although this command shows encryption settings, it will not show any file attributes (Read Only, Hidden, Compressed or System).
Cipher Command Switches
Like many commands in Microsoft Windows, Cipher has several switches that can be found by typing cipher /? at the command prompt window. Below is a listing of this help information as supplied by Microsoft from the aforesaid command (These switches are referenced from the command prompt as stated and on various websites such as Technet). Using these switches in combination produces the results based on your commands.
CIPHER /REKEY [pathname […]]
/B Abort if an error is encountered. By default, CIPHER continues executing even if errors are encountered.
/C Displays information on the encrypted file.
/D Decrypts the specified files or directories.
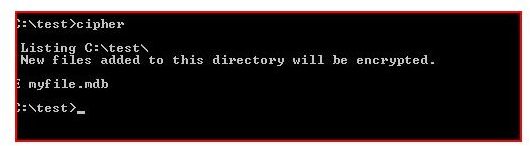
/E Encrypts the specified files or directories. Directories will be marked so that files added afterward will be encrypted. The
encrypted file could become decrypted when it is modified if the parent directory is not encrypted. It is recommended that you
encrypt the file and the parent directory.
/H Displays files with the hidden or system attributes. These files are omitted by default.
/K Creates a new certificate and key for use with EFS. If this option is chosen, all the other options will be ignored.
/N This option only works with /U. This will prevent keys being updated. This is used to find all the encrypted files on the
local drives.
/R Generates an EFS recovery agent key and certificate, then writes them to a .PFX file (containing certificate and private key) and
a .CER file (containing only the certificate). An administrator may add the contents of the .CER to the EFS recovery policy to
create the recovery agent for users, and import the .PFX to recover individual files. If SMARTCARD is specified, then writes
the recovery key and certificate to a smart card. A .CER file is generated (containing only the certificate). No .PFX file is
generated.
/S Performs the specified operation on directories in the given directory and all subdirectories.
/U Tries to touch all the encrypted files on local drives. This will update user’s file encryption key or recovery agent’s key to the
current ones if they are changed. This option does not work with other options except /N.
/W Removes data from available unused disk space on the entire volume. If this option is chosen, all other options are ignored.
The directory specified can be anywhere in a local volume. If it is a mount point or points to a directory in another volume, the
data on that volume will be removed.
/X Backup EFS certificate and keys into file filename. If efsfile is provided, the current user’s certificate(s) used to encrypt the
file will be backed up. Otherwise, the user’s current EFS certificate and keys will be backed up.
/Y Displays your current EFS certificate thumbnail on the local PC.
/ADDUSER Adds a user to the specified encrypted file(s). If CERTHASH is provided, cipher will search for a certificate with this SHA1
hash. If CERTFILE is provided, cipher will extract the certificate from the file.
/REKEY Updates the specified encrypted file(s) to use the configured EFS current key.
/REMOVEUSER Removes a user from the specified file(s). CERTHASH must be the SHA1 hash of the certificate to remove.
How to Encrypt a Folder with a File
In order to encrypt a folder with a file, go to a command prompt and change directories to the area on the ‘C’ drive. Type cipher /e c:\thepath and hit enter. Cipher will now encrypt the folder and any files found in the path you typed. To view the encryption, type cipher at the command prompt. As stated in page one, you will see E for encrypted and U for unencrypted. As shown in the switches above, the /a switch can be used to encrypt individual files.
Windows GUI Encryption
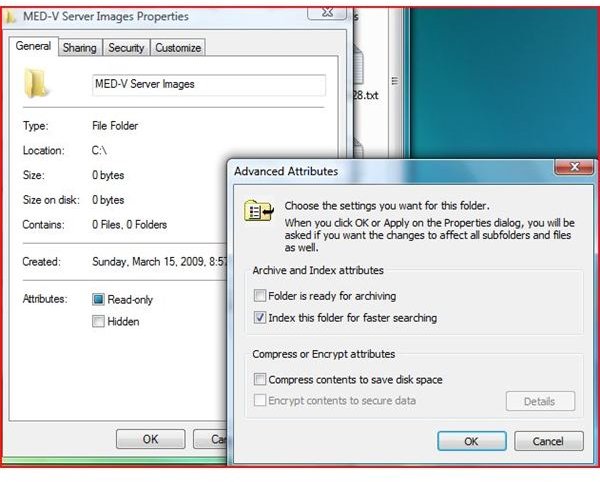
Encrypting a Folder with a File
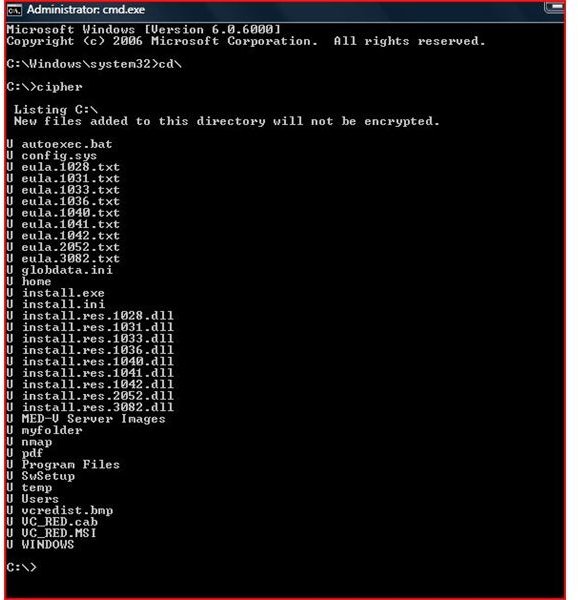
Using Cipher To Help Erase Data
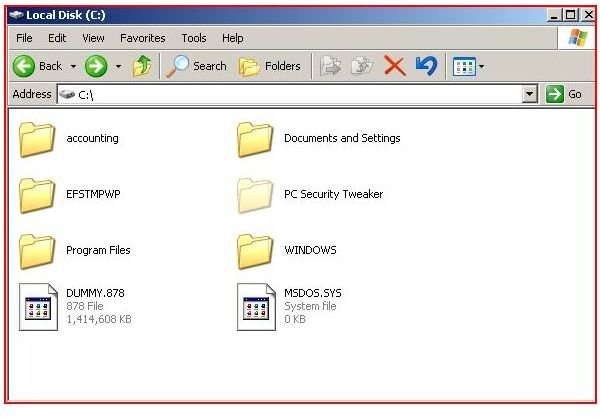
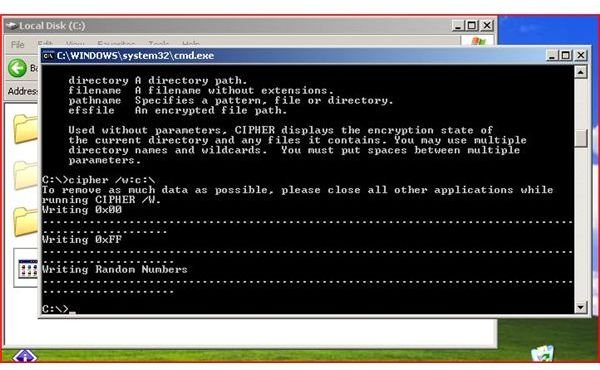
Using Cipher to Clear Deleted Files
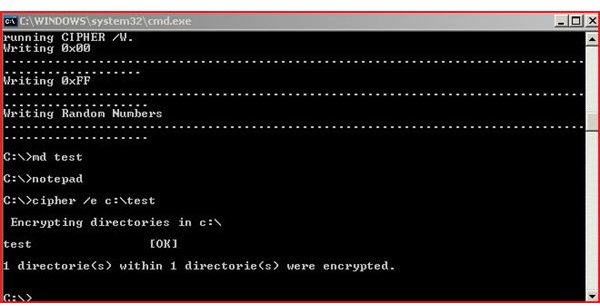
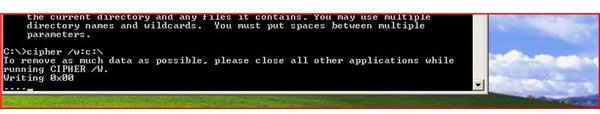
Cipher can be used to delete the deleted files in your free space on your computer. Using the Cipher /w:c:\ command will delete any left over deleted file information. This helps prevent the undeleting of these files at a later time. (See Pictures Below)
How It Works
Cipher with the ‘w’ switch will create a folder named EFSTMPWP. As the process continues, Cipher will write zeros, then ones and then random numbers over the free space, creating a temporary file until the drive is full and then deletes the temporary file. Because files are not truly deleted until the space is overwritten; this process ensures that all space has been erased. This is a key security feature that is almost always overlooked.
Conclusion
Running the cipher command has several advantages. Encryption is not supported on home editions but is on all professional versions of Microsoft Windows. Encrypting files helps to protect data and assets on a computer. Cipher can be used to encrypt databases so to prevent data theft. With proper configuration of file systems, antivirus, individual users and groups during sharing, firewall rules, VPNs and encryption; your data can be secure. Also, using the cipher command to erase free space from formerly deleted files helps to prevent old files from being restored. With the many command line switches with this tool, this command helps to protect critical documents including databases that contain valuable information. These switches help individual users encrypt and provides more powerful techniques to encrypt than the Windows GUI encryption.
For more information, see Microsoft TechNet.