Nmap: Performing Penetration Tests with UMIT
What is Nmap?
Nmap is an excellent network scanning, auditing and penetration tool. Nmap (short for Network Mapper) is free and open source. Because Namp uses raw packets, it determines which hosts are alive on a network and what services and ports are available or open. Nmap uses its unique ability to scan a single host or multiple host on any size network. Because Nmap is open source, any operating system can use this security software. This security software can be ran against any node on a network to ‘see’ the vulnerabilities of the scanned host. Nmap can be used to scan workstations, servers, firewalls, VLANS and many other items on your network.
The most popular version of Nmap is command line driven but Zenmap and UMIT are available for ease of use.
UMIT
What is UMIT?
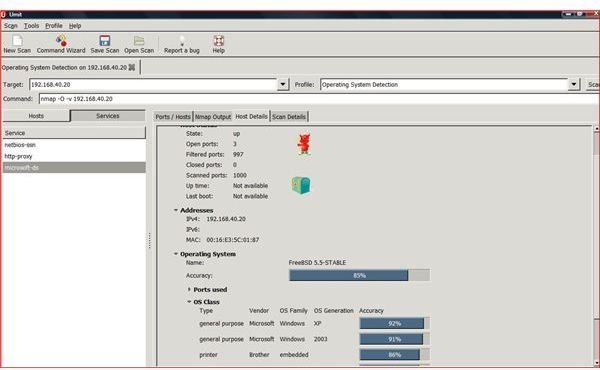
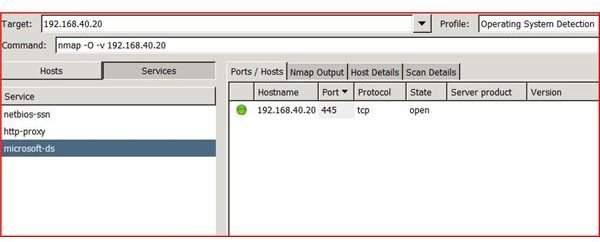
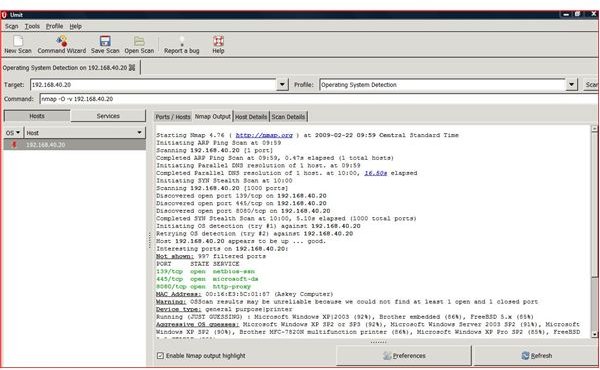
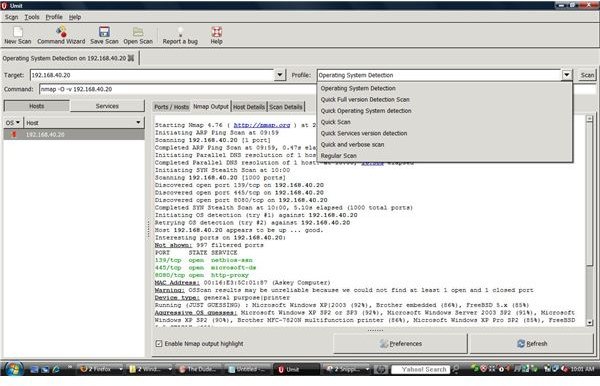
The UMIT project allows for a GUI interface when using Nmap. Umit allows end users to walk through command wizards and a user friendly GUI interface. Each scan that is created can be saved under a profiles portion of the program. The individual scan results allows for the sorting and grouping of scanned results. The Umit interface can be used through the internet and allows for compare modes.
The Umit project is found at SourceForge and is open source allowing for modification of the source code if necessary.
With Umit providing this type of interface for Nmap, network administrators and systems administrators can perform more accurate penetration tests of workstations or servers on their network. Umit now provides scan scheduling, network inventory, a radial mapper and many more features.
Umit Project Link
Using UMIT
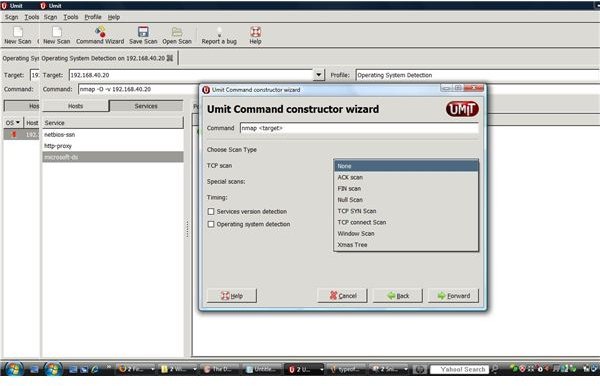
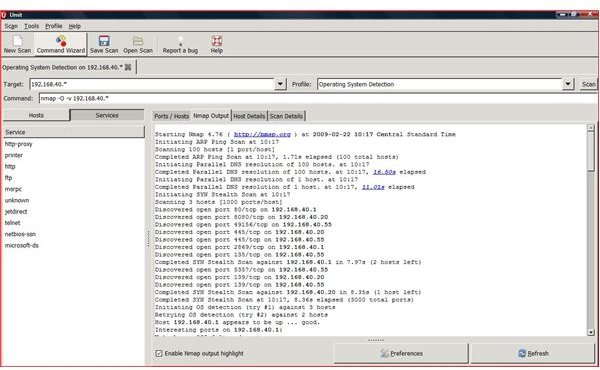
Conclusion
This tool is a tool that should also be used with caution. This powerful software could be used in a malicious manner and should only be used as it was intended.
NMap offers an endless array and combination of switches to scan hosts on a network. With UMIT, this process is very simple and user friendly. Systems Administrators, Network Administrators, and Security Analysts should use this tool to scan all devices to find any ‘holes’ and ‘vulnerabilities’ on devices in their network. Scanning can set off ‘alerts’ and alarms on your IDS system. This can act as a ‘check’ against this important intrusion server. Any change or upgrade to an operating system can create a new vulnerability.
Organizations should include penetration testing in their policy and procedures. This software should be included in any training of your security analysts. This important part of security cannot be overlooked and should be performed on a regular basis.
Many organizations seek ISO’s 27001 endorsement and certification. While this certification can be very detailed, it is important to train and implement the standards even if your organization is not seeking the certification. It is tools such as this that will make your organization secure.
