Overview: Physical Security Controls Page 1
What are Physical Security Controls
Administrative controls rely on the willing compliance of managers and employees. Physical controls rely on the proper application of physical barriers and deterrents to control behavior. It’s through the use of physical controls that an organization controls physical access to facilities and systems. They also assist in maintaining the operating environments necessary to continue information processing and delivery activities.
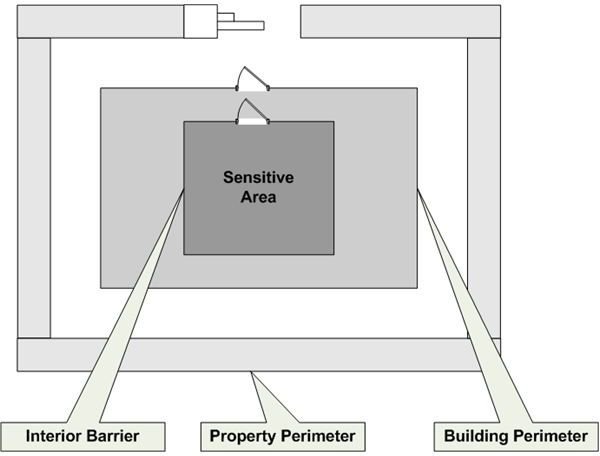
Before moving into the specifics of various physical controls, it’s important to understand their proper application and purpose. Figure 1 is an example of one way to view the layers of a physical security solution.
Physical security controls are meant to detect and delay the passage of an intruder as he or she moves inward toward sensitive areas within around or within a facility. Following the principle of diversity in design, the use of different controls at each entry point helps to attain this objective.
Preventive Physical Security Controls
Preventive physical controls provide an environment in which to safely process information as well as barriers to unauthorized access to systems. These controls include:
- Alternate power sources
- Flood management
- Data Backup
- Fences
- Human guards
- Locks
- Fire suppression systems
- Biometrics
- Location
Alternate Power Sources
Under normal circumstances, it’s reasonable to rely on the power company as a clean, stable source of power. But as we’ve all experienced, there are no guarantees that the power coming into your building will always be available. Alternate power sources are used to provide power when utility power fails.
In this section, we’ll discuss two types of power sources: uninterruptible power supplies (UPS) and generators. A UPS is a battery powered device that provides power for a short period. It is typically used to provide power long enough to properly shut down your servers (preventing data or system damage) or to switch to a generator. You shouldn’t rely on your UPS to indefinitely continue normal operations.
If you must keep one or more servers up during a long-term power outage, consider a generator. With a continuous supply of fuel, a generator can indefinitely supply power to your data center. Because switching to generator power can take a few minutes, it’s necessary to supplement your generator with a UPS to prevent a hard shutdown of your data center equipment; the UPS provides power for the time it takes to bring your generator online.
Flood Management
The first preventive measure to keep water out of your facility is locating it in a geographic area that doesn’t regularly flood. Next, you should place water sensors in your data center. If you have raised floors, place them under the floor. If not, place them in areas most likely to experience flooding first. Detecting the presence of water in your data center might not allow you to do anything to continue operating, but it can provide enough warning so you can protect your equipment from damage. This process can consist of removing equipment from the affected area or simply shutting down equipment that’s impractical to move. In either case, damage is minimized, allowing your business to quickly return to normal operation.
You should also consider mounting your servers at least two to three inches above the floor. Purchasing racks in which to place your servers should make this a simple task.
Data Backup
For the past 17 years, I’ve taught the engineers and analysts working for me that the most important task they perform each day is ensuring the proper backup of critical business data. Backing up your systems is the single most important activity you perform if you want to have any chance at all of recovering from a system, data center, or facility failure.
In this section, we’ll discuss three types of backups: full, incremental, and differential. A full backup copies all files from your production storage devices (normally disk) to your backup media. Although tape has been the backup media of choice for many years, backup to disk is also popular. A full backup provides for the fastest restore time. If you have to rebuild a server in your data center or at a disaster recovery location, you only have to restore a single backup. However, many organizations can’t perform full backups every night.
Full backups take a long time to run. If you run production jobs twenty-four hours a day, or if you have to stay in the office until the backups are complete, full backups every night might not be the best option. Incremental and differential backups can help.
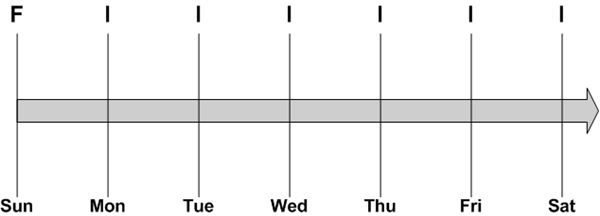
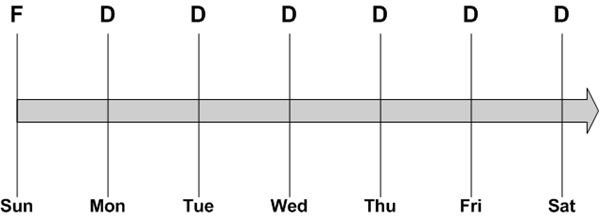
An incremental backup copies to your backup media all files that changed since the last backup. This requires a much smaller backup window. But it takes much longer to restore if you have to rebuild a system. Figure 2 depicts a common incremental backup schedule.
In this example, a full backup is performed each Sunday night when there are no production jobs running. An incremental backup is run on each of the other nights of the week. This is a great solution for minimizing production downtime. But what happens if the system backed up in this way fails?
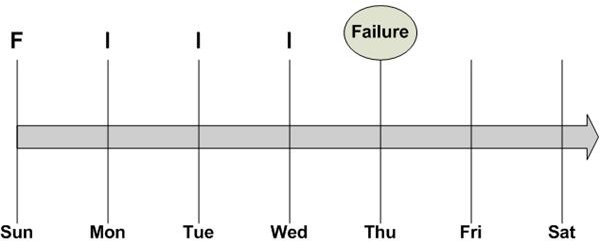
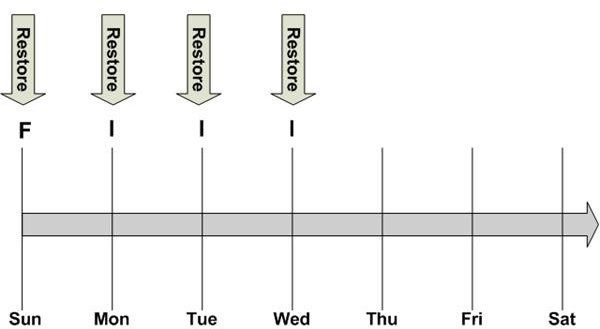
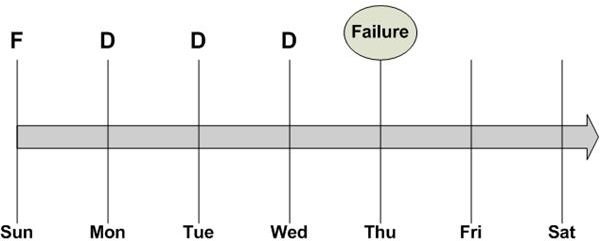
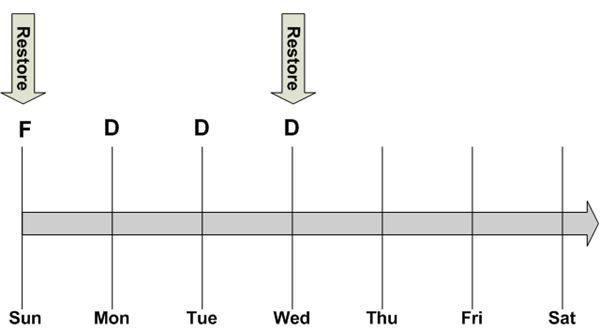
In Figure 3, the system fails on Thursday, prior to the Thursday night backup. Since the backups on Monday, Tuesday, and Wednesday contain only the files that changed since the previous night’s backup, the data center staff must restore the full backup from Sunday, followed by each of the incremental backups in the correct sequence. The restore process is depicted in Figure 4. This takes awhile and may not be the best backup method when restoring systems critical to business operations.
Differential backups provide a backup and restore solution that combines a measure of the reduced backup time of incremental backups with a portion of the reduced restore time inherent in a full backup method. A differential backup copies to your backup media files that have changed since your last full backup.
Figure 5 represents a typical differential backup schedule. It looks the same as the incremental approach in Figure 2. However, there is one important difference. Since the differential backups copy all files that have changed since the last full backup, the backup time increases as each day passes; more files are changed as the week progresses. But the restore time is usually much shorter than either full or incremental backups.
Figure 7 depicts a differential restore with a system failure on Thursday, prior to the Thursday backup. Instead of a full restore and three partial restores, a differential restore consists of a full restore and the restoration of the last differential backup.
Once you create your backups, you need to keep them in a safe place. A fireproof safe in your data center might seem like a good idea. But what happens if your data center is destroyed or is inaccessible? How do you get to your tapes? At least one set of recovery tapes should be kept at an off-site location. For example, if you perform incremental backups, the last full backup and all subsequent incremental backups should be kept in a secure off-site facility. Even if your primary backup method is to disk, you should have a full recovery set of data at another location.
Many small businesses are beginning to implement an over-the-Internet solution that solves both the backup scheduling and off-site storage challenges. Services like EMC’s Mozy provide backup storage, accessible via the Web. Businesses can schedule backups of all or just modified files, in target folders, to encrypted offline storage.
The final backup planning consideration is the protection of the information stored on tapes. Tapes can be stolen or lost. Sensitive information, like health information protected under the HIPAA, can be compromised. You should consider encrypting sensitive information as it’s copied to tape. Most, if not all, backup software supports this feature.
Fences
Fences are a physical barrier used primarily to deter casual trespassers. Most organizations are not prepared to install eight foot fencing topped with razor wire. Unless you are working on products essential to national security, this kind of barrier can present an overwhelming image to potential customers; not to mention the rapid depletion of your security budget.
To a casual intruder, a fence of any kind communicates the presence of a no-trespass zone. Fencing by itself is not very effective against a determined intruder. But coupled with other controls, it can be a component of a very effective physical security plan. Controls that can be used to supplement fencing include continuous lighting, closed circuit cameras, physical intrusion detection devices, and guards.
Human Guards
Guards, both roving and stationary, provide a control that can react to the unexpected. With all the technology available today, a human being still adds the most value when intuition and common sense are required. Further, once an intruder decides to penetrate your physical perimeter, guards are the best defense against his actually reaching your assets. The obvious downside is cost. Costs associated with hiring, salary and benefits, equipment and uniforms, training, etc. must be weighed against the potential business impact of a physical intrusion. When hiring your own guards isn’t an option, consider unattended physical safeguards that alert local law enforcement.
Locks
We’ll cover three common types of locking mechanisms in this chapter - badge readers, combination locks, and push-button/cipher locks.
Badge readers are electronic devices that may or may not be connected to a central security system. Central security systems facilitate efficient management of authorized access and the monitoring of entry points.
A card, or badge, is used to release a lock controlled by the reader. Based on the type of reader used, lock release can occur by direct contact with the reader or through proximity detection.
Security systems based on badge readers are often easy for users to operate. A simple swipe of a card or simply walking up to a proximity activated reader can facilitate entry. There’s no combination to remember or key to locate. A disadvantage of a badge system is cost, including the purchase of the readers and the purchase, issuance, and tracking of the badges. A bigger problem may be that the unreported loss of a badge or token might compromise your physical security efforts.
Two basic types of locks used to secure physical assets when badge systems are not used are key locks and keyless locks. A key lock can be a simple lock affixed to a door (deadlock, handle locks, etc.) or a padlock. Key locks are inexpensive, and your users are familiar with their use. A disadvantage with using key locks is the management of keys. One lost key, and all affected locks must be replaced. There is also the risk that keys will be lost or reproduced without your knowledge; thus elevating the risk of unwanted physical access.
Keyless locks include:
- Mechanical and electronic rotary combination locks
- Mechanical Push-button locks
- Cipher locks
Rotary combination locks are another familiar locking method. Authorized users are provided a combination. Mechanical, rotary, and combination locks are inexpensive and easily replaced if an employee leaves the company or if you believe the combination was shared with unauthorized personnel. Although electronic rotary locks are not inexpensive, changing the combination is easily accomplished by a lock administrator.
Push-button locks are mechanical devices with numbered buttons. A person seeking to gain access to a secured area enters a code to release the locking mechanism. Changes to the combination are often made by disassembling the lock.
Cipher locks are roughly the electronic equivalent of a push-button lock. Although more expensive than its mechanical counterpart, the cipher lock provides significant advantages. Several different access codes can be entered into the lock. Using a lock that supports multiple codes enables access for each authorized user with a unique code. And you can assign a special lock administrator code for code maintenance.
Many cipher locks also support a panic code. Users approaching the lock under duress enter the panic code, initiating an audible or silent alarm. Some cipher lock systems are connected to a central access control computer. Like many badge systems, this provides for centralized management of access codes, access monitoring, etc.
The obvious disadvantage of combination and push-button/cipher locks is the possibility that a combination or code will be compromised. One method an intruder might use to obtain a combination or code is shoulder-surfing. Another is the use of social engineering.
Although locks are the most common method used to secure physical assets, they should be considered only as a delaying tactic. Locks are quite vulnerable to the efforts of a determined intruder. In addition to the possible compromise of keys, combinations, badges, or codes, a good crowbar may be “good enough” for quick entry into one of your locked areas.
Fire Suppression
It might seem odd that a discussion of fire suppression systems occurs in a section on preventive controls. But consider that an effective fire suppression system can help prevent the destruction of your information infrastructure and, more importantly, injury to your employees.
A common type of fire suppression system is the ubiquitous fire extinguisher. Fire extinguishers are not intended to serve as your primary means of containing facility fires. Instead, their purpose is to assist in getting personnel out of affected areas.
Mount extinguishers in plain view. Train one or more of your employees in their use. Quarterly inspections by a certified fire extinguisher servicing agency or company should be an essential part of your fire suppression strategy.
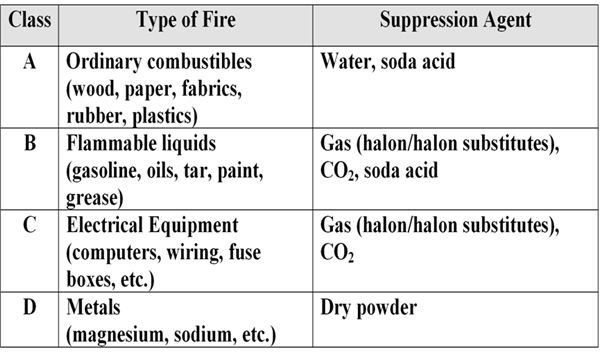
Another important consideration is the deployment of the proper types of extinguishers. For instance, the type of fire extinguisher installed in your data center may not be appropriate for a manufacturing plant floor. Table 1 lists fire suppression system classes and the types of fires for which they’re intended.
We’ve established that fire extinguishers are not intended to actually suppress a large scale fire in your facility. That’s the function of a fire suppression system integrated into your building’s infrastructure. This type of system is designed to quickly distribute a fire suppression agent over a large area. Two major types of systems that fall into this category are water and chemical.
Water systems are an effective, inexpensive solution for areas where Class A fires are common. Your general office area is a good example. Water-based suppression systems deliver water to a fire via standard sprinkler heads or by using deluge style heads. Deluge solutions deliver large amounts of water quickly. In addition to how the water is delivered, there are two approaches to how a suppression system stores water - wet pipe and dry pipe.
Wet pipe systems store water in the pipes feeding delivery heads. The advantage of this approach is the lack of delay in getting the water to where it’s needed. The disadvantages associated with using wet pipe systems include:
- Water freezing in the pipes if proper environmental controls are not used or available
- Condensation build up causing water damage to computer equipment
Dry pipe systems help solve these problems. In dry pipe systems, valves prevent the distribution of water into the pipes feeding distribution heads until a fire is detected. Upon detection of a fire, the valves open and water flows to the heads for release. This type of system is ideal in areas where pipes may freeze or in data centers where water damage from leaks or condensation may occur.
Although water-based systems are typically less expensive than chemical delivery systems, they are not the best choice for data centers. Aside from the fact that water delivered to extinguish a fire may cause more damage than the fire, there is the problem of false positives by your fire detection sensors.
More than once I’ve been involved in dealing with fires that didn’t exist. Fire detectors are not infallible. In one instance Inergen, a chemical suppression agent, was delivered to my data center because two detectors under the raised floor interpreted a cooling unit gas leak as the presence of a fire. It took 14 hours to clean and bring the systems back to full production. If water had been delivered instead, it may have been necessary to transfer to our hot site until I could assess and replace my 250 servers, storage arrays, etc. If your budget requires the use of a water delivery system, consider the installation of a preaction solution.
Preaction water delivery solutions are very similar to dry pipe systems. The difference lies in what happens after the water is distributed to the distribution heads. In a preaction system, the suppression agent is not immediately released. For example, the actual presence of a specific level of heat might be necessary before water is dispensed to affected areas. This provides time to take steps to cancel false alarms.
Chemical delivery systems are a much better choice to protect your data center. Since no water is released, there is little or no damage to critical systems. Recovery is faster, and the loss of critical data is minimized. Agents used in non-water systems commonly include FM-200, Inergen, and CO2. The primary disadvantage associated with the implementation of a chemical-based system is cost. However, the additional cost provides the assurance of a reasonably quick recovery following a less than catastrophic fire.
Biometrics
Biometrics is the use of unique human physical characteristics to iverify the identity of authorized personnel. You can use these devices to control doors, gates, etc. Although I’m presenting a detailed discussion of biometrics as they apply to physical access controls, all the principles discussed also apply to biometrics-based network or device login.
There are several human physical traits that can be used to uniquely identify a person. They include:
- The retina, specifically the blood vessel pattern inside the eye
- Voice patterns
- Signature dynamics
- Finger or hand geometry, including finger prints, finger or hand height and width, etc.
- The features of the iris, the colored area of the eye surrounding the pupi
Of these, the iris, retina, and finger/hand geometry are the most effective. A person’s voice may be recorded and signatures can be forged.
When considering the purchase and implementation of a biometrics identification system, you should address the following eight critical success factors:
- Accuracy
- Speed
- Resistance to counterfeiting
- Reliability
- Data storage requirements
- Enrollment time
- Perceived intrusiveness
- User Acceptance
Accuracy
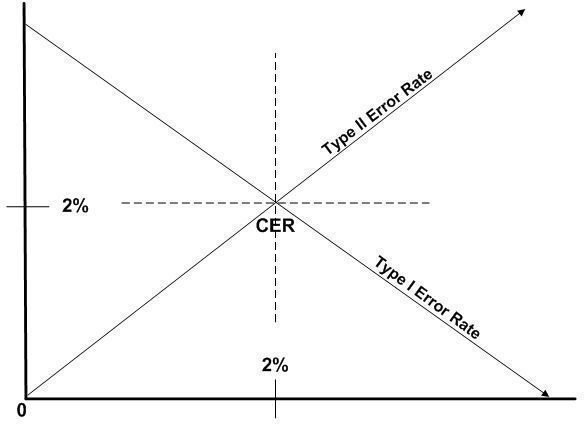
Biometric devices have improved significantly over the past several years. However, there are still no guarantees of 100% accuracy. It’s your responsibility to select the level of inaccuracy that you and your employees can tolerate. When judging error rates, consider the principle types of errors - Type I and Type II. Type I errors include all instances in which a biometric system denies access to an authorized user. The identification of an unauthorized user as an authorized user is an example of a Type II error. By adjusting the sensitivity of the biometric sensor, you can increase or decrease the occurrence of each error type. However, as you decrease Type I errors, you might increase Type II errors. The opposite is also true.
The key objective in implementing a biometric system is the proper balance between the two error types. The most common method is to focus on the Cross-over Error Rate (CER). See Figure 8. This is the point at which the frequency of Type I errors and the frequency of Type II errors are equal. When shopping for the right system for your business, the CER is the best indicator of overall accuracy.
CER is expressed as a percentage. Lower values are better. Values of two to five percent are generally considered acceptable.
Speed
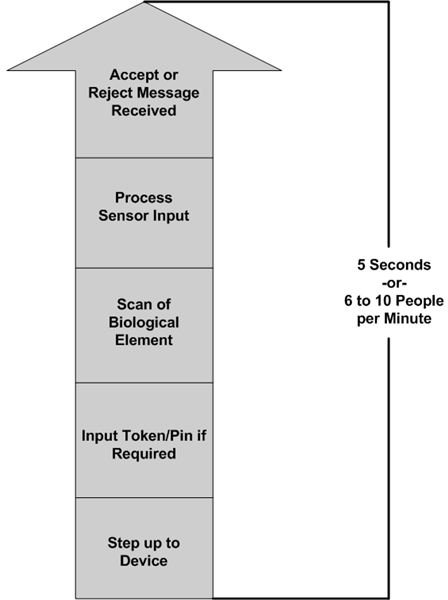
When considering the probability that your users will accept the use of biometrics, the speed at which a sensor and its controlling software accept or reject authentication attempts is the most important factor. The effective throughput, or how many users a biometric sensor can process in a given period, is a function of the entire authentication process. Figure 9 depicts the several stages involved. Acceptable throughput is typically five seconds per person or six to ten people per minute. User frustration begins to set in at lower throughput rates.
Resistance to counterfeiting
Again, signature dynamics and voice recognition are not necessarily the best choice for biological recognition because of the potential for forgery or the use of recorded voice. But systems that use other body parts might also be susceptible to counterfeiting. For example, some early biometric systems allowed an intruder to use lifted finger or hand prints to gain entry. Today’s systems are, in general, more sophisticated. Make sure to ask the right questions if you consider using a biometric access control system. When possible, request a demonstration of the system’s resistance to counterfeiting.
Reliability
Sensors must continue to operate at a low CER between failures. A gradual degradation in throughput affects user acceptability and organizational productivity.
Data storage requirements
The amount of storage necessary to support a biometric system depends on the data stored. Voice recognition systems might use a great deal of storage; voice files are usually large. Current finger architecture recognition technology, however, stores a relatively small hash value created when a user is enrolled. Whenever a sensor scans the finger again, it recomputes the hash value and compares it to the stored value. Whatever biometric solution you choose, make sure you understand the impact on your storage environment.
Enrollment time
Another factor influencing user acceptance is the time required to enroll a new user into the biometric system. An acceptable enrollment duration is usually two minutes or less per person. This enrollment rate not only reduces employee frustration. It also helps reduce administrative costs associated with system management.
Perceived intrusiveness
Second only to throughput, the amount of personal intrusiveness a sensor presents to your employees is a major determinant when assessing user acceptance. The following is a list of common fears that grow out of biometric implementations.
- Fear that the company stores unique personal information
- Fear that the company is collecting personal health information (retinal scans look at patterns that are also used to determine certain health conditions) for insurance purposes
- Fear that the red light in retinal scanning sensors is physically harmful
- Fear of contracting diseases through contact with publicly used sensors
The best way to deal with these issues is to hold open and honest discussions about how the systems work, the health risks involved, and how the organization plans to use the information. Remember, user acceptance doesn’t depend on how you perceive biometric authentication. Rather, it depends on how your employees perceive it.
Location
The geographic location of your facility plays a large role in the level of risk your business faces due to physical threats. Frequent storms, power outages, and a high crime rate are all examples of things to consider prior to selecting a location for your organization. Other issues include proximity to police and fire services. Quick reaction times associated with security events usually equate to reduced business impact.
Tables and Figures (Hover for caption, click to enlarge)
Key Terms
Hash Value - A hash value is produced by feeding information to a special computer program. The program converts the input into a fixed length value. The same input should always produce the same hash value. In the case of biometrics, a significant amount of information may be gathered by a finger sensor. This information can be reduced to a much smaller hash value. Another advantage of using hash values instead of raw information is the inability of an attacker to derive from the hash value the original input from which it was created.
Proximity detection - Some security devices used for physical or logical access control can detect, without physical contact, the presence of an individual authorized to gain entry to a facility or to log in to a workstation. These are called proximity detection devices. A proximity detection solution normally consists of a reader at the point of entry, or at the workstation, and a badge or other device in the possession of the employee. When the reader and the employee are within a predefined distance of each other, the user is authenticated to an access control system.
This post is part of the series: Overview of Physical Security
This is a series of two articles discussing the purpose of physical security, common controls, and how to implement them.