Introduction to Local and Wide-area Networks - Part 2
TCP/IP
A MAC address (covered in Part 1) is fine for moving data around the same network segment. But it doesn’t work very well when you want to send data to another segment. When traversing multiple network segments is necessary, using the TCP/IP suite of protocols is the most common way to get it done.
TCP/IP (Transmission Control Protocol/Internet Protocol) is used by the Internet and by most businesses to move information between network segments. One major advantage of using a common set of protocols to move information over the Internet is a seamless integration with vendor and customer networks connected via a common global network. A major disadvantage is the ease with which malicious hackers can use this global connectivity to spread malicious programs.
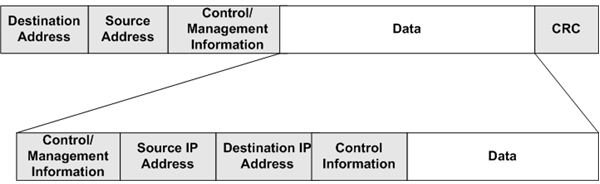
TCP/IP uses an IP addressing scheme to route packets from one network segment to another; it’s known as a routable protocol. Figure 1 shows where the TCP/IP information is located in an Ethernet Packet. As you can see, the Data segment is actually an IP Datagram.
Some of the items contained in the Control/Management section of the Datagram are,
- The version of TCP/IP used to construct the Datagram
- The length of the Control/Management section of the Datagram
- The length of the Datagram
- Time to Live (This is defined as the number of routers a packet can pass through before it’s expired, also measured as “hops”.)
The Source IP Address section contains the IP address of the sending device. The IP address of the target device is contained in the Destination IP Address section. The second Control section may contain additional information about how to process the Datagram, or it can be omitted. The Data section contains some additional management information as well as the actual application or file information being sent.
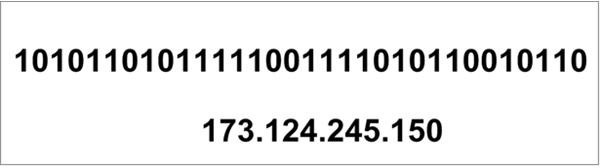
An IP address consists of four sets of eight bits called octets, but network engineers usually write the address in dotted decimal notation. Figure 2 shows both the binary and the dotted decimal formats for an IP address. Although a network device can easily divide and interpret the binary version of an IP address, we humans aren’t quite so adept at manipulating Base 2 values. Luckily, we can use dotted decimal notation to simplify the process.
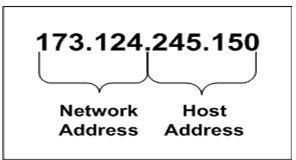
One or more of the octets in an IP address represent the address of the network or network segment to which a device is connected. The remaining octets uniquely identify the device (e.g., laptop or desktop computers) In the address shown in Figure 2, the first two octets specify the network on which the target device resides. The second two octets, or the host address, uniquely identify a device on that network. See Figure 3.
So how does a network device know which octets represent the network portion of the address? This is accomplished by using a subnet mask. When configuring a network device with an IP address, you must also include a subnet mask. The mask tells the device how to split up the address. In our example, we used a mask of 255.255.0.0. Note that the mask is also presented in dotted decimal notation.
When the device applies the mask to the address, it treats each bit location where the mask contains a 1 as part of the network address. By applying the mask to the address, the device can determine the network address contained within the IP address. See Figure 4.
We’ve covered the basic principles of data formatting and network addressing. In the next article, we’ll see how to apply this knowledge to learn how networks work.
See other articles in this series…
Tables and Figures (Hover for caption, click to enlarge)

This post is part of the series: Introduction to Local and Wide Area Networks
Understanding how networks work is an important first step in understanding information security. This series provides everything you need to know to get started.
- Introduction to Local and Wide-area Networks - Part 1
- Introduction to Local and Wide-area Networks - Part 2
- Introduction to Local and Wide-area Networks - Part 3
- Introduction to Local and Wide-area Networks - Part 4
- Introduction to Local and Wide-area Networks - Part 5
- Introduction to Local and Wide-area Networks - Part 6
- The Importance of Wireless Connectivity