Information Security Vulnerability: Assessment Methodology
Identifying Critical Vulnerabilities
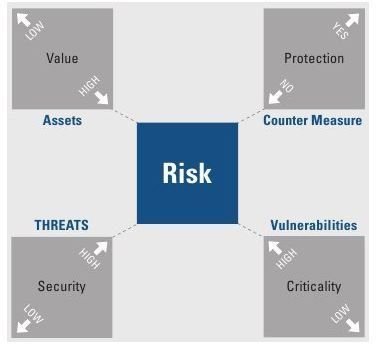
In order to evaluate any information security vulnerability, assessment methodology begins by identifying the risk. You start by reviewing key information and classification levels to see what weaknesses exist. Begin by creating a topology of the system–that is, look at how the system interacts and interconnects. You can use network diagrams, accounting and finance assessment information, or marketing plans; in other words, look at the business structure to identify its strengths and weaknesses.
At the information or IT level, look at the construction of the network. How are passwords constructed; are they strong or weak? Does the network have a firewall? Does the network have a virus protection program? These conditions are important because the vulnerabilities that come from exposure to the Internet can affect the organization’s ability to perform its more fundamental business tasks. Those tasks are in accounting and finance, sales and marketing, or manufacturing and engineering. If the network or computers break down, what business functions can be done without them? If the answer is very little, then these vulnerabilities are critical.
In general, the most critical information security vulnerabilities are those that can shut down the business. They could be network based, hardware based, or software based. However the cause, the result is data loss or performance.
Image Source: Creativity Central
Assessing Internal and External Vulnerabilities
The result of the vulnerabilities uncovered will lead an organization to ask how can data loss occur? Where is the data sent, by whom, and what are the mechanisms involved? Internal exposure can come from well meaning employees who may take work home with them. They may expose the company to viruses or other malware by using flash drives or other hardware platforms that seem innocent enough. They may copy files that are confidential to work at home with them, but by so doing they open the file to malware.
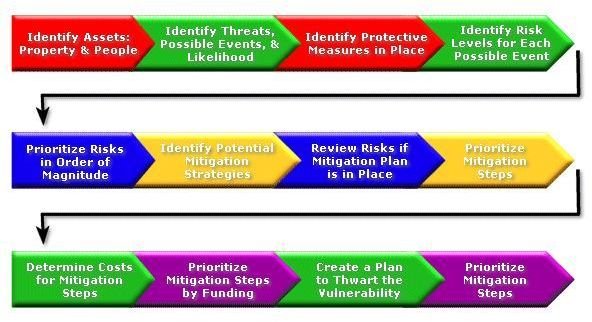
Another vulnerability that is external comes from a weak or non-existent firewall. Anyone, under these circumstances, can access the nework and compromise the system. Failure to keep up with security patches issued by Microsoft or other software manufacturers can expose the system.
An external weakness can come from not maintaining and updating the virus dictionary. Since viruses have a tendency of modifying their appearance, updates that can identify them need to be maintained; otherwise the virus firewall will have holes.
Image Source: elert.com
See Also: Duties of an Information Security Officer
Summary
Information technology vulnerabilities can cause a business to lose data as well as to perform its operations poorly. To assess the vulnerabilities one must first identify the areas of weakness. This can occur from an internal or external position. The vulnerabilities could come from a department or an activity or an individual.
Once the vulnerabilities are identified, then the task is to assess how they impact a business. The critical question to ask is how will the business perform if the vulnerabilities are not addressed or fixed? If the business continues to perform normally with little or no interruption then it is not serious. On the other hand, if it is a show stopper, then the vulnerability must be addressed immediately.
Source: Deloitte. How to build a security program that meets your business needs, at https://www.deloitte.com/view/en_CA/ca/services/enterpriserisk/securityandprivacyservices/article/f8d733d0303fb110VgnVCM100000ba42f00aRCRD.htm.
See Also: Top 5 Free Network Security Tools